HTTP Request Smuggling – Identifying Frontend Request Rewriting and Exploiting
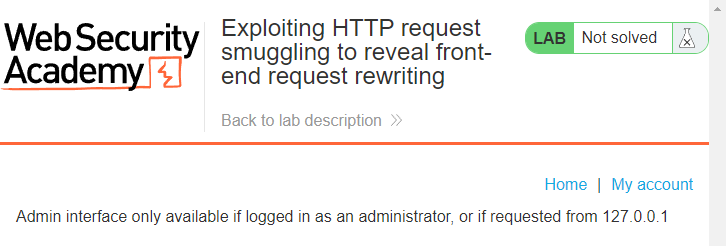
This is the 7th blog post in the series I am publishing dealing with Request Smuggling or Desync vulnerabilities and attacks. These posts align to the PortSwigger Web Security Academy labs (here). Just as in the past two posts, this…





