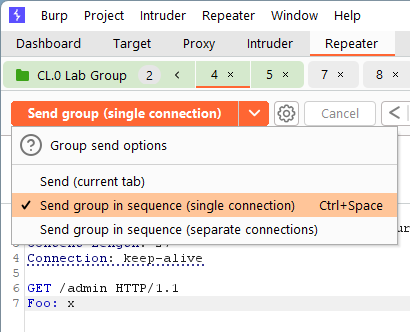
HTTP Request Smuggling – HTTP/2 Request Tunnelling
Time for another one of the advanced labs on the PortSwigger Web Security Academy. For this lab, we are dealing with an HTTP/2 downgrade attack that allows the attacker to smuggle a request to the backend. Due to how the…